The Shield of Protection: Strategies in IT Security
Explore cutting-edge IT security measures to safeguard your digital assets. Learn about encryption, threat detection, and best practices for a resilient cyberdefense

Cybersecurity is definitely a trending topic these days. With numerous cyber threats out there, it's crucial to improve our digital defenses. Our personal information and business data are constantly at risk!
That's why it's absolutely necessary to have strong IT security measures in place. It's similar to securing our digital doors with a lock, making sure our possessions are protected from those annoying people on the internet. Whether we're interacting in conversations, completing transactions, or working, defending ourselves online is of crucial importance. So, let's remember to keep our software up to date, utilize strong passwords, and remain aware! Together, We all have the power to make the internet a safer place.
As technology becomes more advanced, the challenges of dealing with online threats also become more intricate. This poses a great complexity for both individuals and businesses. It increases the probability of falling victim to cyberattacks, which can result in the exposure of private information, financial losses, or damage to one's reputation. As the online world becomes more advanced and intricate, it is crucial for everyone to exercise and be careful, and take necessary measures to ensure their safety and protect their valuable information. The rise of social media and the increasing amount of personal information that people share online has made it easier for cybercriminals to target their victims. Social engineering tactics, such as scam emails that appear to come from a trusted source, can be highly effective in tricking people into giving away sensitive information.
To overcome these challenges, individuals and businesses must take a proactive approach to online security. This includes using strong passwords, keeping software and antivirus programs up to date, being cautious about what information is shared online, and using two-factor authentication whenever possible. It also means staying informed about the latest threats and taking steps to educate others about online safety
The Complexities of Cyber Threats:
1. Technology Complexity:
- Quick Technological Progress: The constant evolution of technology introduces new tools and possibilities, but it also opens doors for more complex cyber threats. Advancements in artificial intelligence, the Internet of Things (IoT), and cloud computing, among others, create a broader attack surface for cybercriminals.
- Universal Impact: This complexity isn't limited to certain sectors or demographics. It affects everyone—individuals managing personal devices and information, small businesses handling customer data, and large corporations dealing with huge amounts of sensitive information.
2. Heightened Cyber Vulnerability:
- Growing Risks: The intricate nature of these cyber threats increases the chances of successful attacks. More sophisticated malware-targeted phishing schemes and ransomware attacks capitalize on the complexities of modern technology, making individuals and organizations more susceptible.
- Consequences: Falling victim to cyberattacks can lead to devastating consequences. Private information exposure threatens individuals' privacy, financial losses can cripple businesses, and reputational harm can erode trust built over years.
3. Necessity for Vigilance:
- Critical Caution: In such a complex online environment, caution is not just advisable—it's a necessity. Individuals and organizations must adopt a proactive stance toward cybersecurity, recognizing that the threats are constantly evolving.
- Protecting Valuable Assets: Safeguarding valuable information—be it personal data or sensitive corporate information—requires a commitment to staying informed, implementing best practices, and investing in robust security measures.
4. Proactive Security Measures:
- Comprehensive Defense: In order to deal with the changing threat perspective, adopting stringent security protocols becomes important. This includes employing the latest cybersecurity tools, regularly updating software and defenses, and implementing multi-layered security strategies.
- User Education: Educating individuals about potential threats and the importance of secure practices is vital. It empowers users to identify and respond to potential risks effectively.
5. Cultivating Cybersecurity Awareness:
- Building a Culture: Creating a culture of cybersecurity awareness is an ongoing process. It involves not only implementing technical solutions but also fostering a mindset where security is ingrained in every action and decision.
- Proactive Preparedness: Staying ahead of potential risks means being proactive rather than reactive. Regular training, simulated exercises to handle cyber incidents, and staying updated on emerging threats contribute to proactive preparedness.
Why is it crucial for individuals and businesses to prioritize and invest in effective cybersecurity measures?
The Crucial Layers of IT Security Defenses.
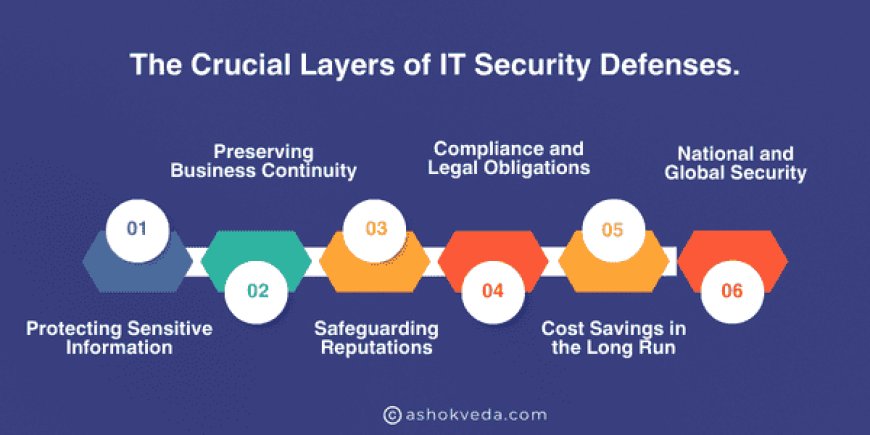
Protecting Sensitive Information: Robust cybersecurity measures act as a shield, safeguarding a plethora of sensitive data types. It encompasses personal information like addresses, social security numbers, and medical records, financial details such as bank account information, and intellectual property like trade secrets and patents. This protection is pivotal in preventing identity theft, financial fraud, and unauthorized access, ensuring the confidentiality and integrity of sensitive data.
Preserving Business Continuity: The impact of cyberattacks on business operations can be staggering. Downtime resulting from breaches or attacks not only disrupts regular workflow but also leads to significant productivity losses and revenue setbacks. Robust security measures, however, serve as a safety net, ensuring that even in the face of potential threats, business operations continue seamlessly. Continuity plans and resilient systems mitigate the fallout of attacks, reducing the detrimental effects on productivity and revenue.
Safeguarding Reputations: Trust and credibility are invaluable assets for any organization. A data breach or security incident can severely damage an organization's reputation. Beyond protecting data, investing in cybersecurity is an investment in maintaining trust and credibility with customers, partners, and stakeholders. Upholding a reputation for strong security practices fosters confidence and loyalty among stakeholders, essential for sustained success.
Compliance and Legal Obligations: In today's regulatory landscape, various industries are bound by strict data protection regulations and standards. Adhering to these regulations through robust cybersecurity practices is not just beneficial but imperative. Compliance ensures that organizations avoid legal repercussions, fines, or penalties associated with failing to protect sensitive information as mandated by regulatory bodies.
Cost Savings in the Long Run: While implementing robust cybersecurity measures incurs initial costs, the potential financial losses resulting from a successful cyberattack can be devastating. The expenses associated with data breaches—remediation, recovery, legal fees, and fines—far exceed the initial investment in preventive measures. Proactively securing systems and data ultimately leads to significant cost savings in the long run.
National and Global Security: Cybersecurity transcends individual or organizational concerns; it is a fundamental component of national and global security. Protecting critical infrastructure and sensitive information on a larger scale is essential for geopolitical stability. Collaborative efforts among nations to fortify cyber defenses are crucial in safeguarding against cyber threats that may have far-reaching implications for global security.
cybersecurity is super important. It's not just about keeping secrets safe and making sure businesses keep running smoothly. It's also about keeping people's trust, following the rules, saving money, and making the whole world safer. Everyone, whether it's regular folks or big companies, needs to realize how vital cybersecurity is in today's connected world. It helps us stay safe from all the different kinds of bad stuff that can happen online. The more we pay attention to it, the better we can protect ourselves from all the tricky things that might try to cause problems.